1. Trusted Firmware M¶
Trusted Firmware-M (TF-M) implements the Secure Processing Environment (SPE) for Armv8-M, Armv8.1-M architectures (e.g. the Cortex-M33, Cortex-M23, Cortex-M55 processors) and dual-core platforms. It is the platform security architecture reference implementation aligning with PSA Certified guidelines, enabling chips, Real Time Operating Systems and devices to become PSA Certified.
TF-M relies on an isolation boundary between the Non-secure Processing Environment (NSPE) and the Secure Processing Environment (SPE). It can but is not limited to using the Arm TrustZone technology on Armv8-M and Armv8.1-M architectures. In pre-Armv8-M architectures physical core isolation is required.
Trusted Firmware-M consists of:
Secure Boot to authenticate integrity of NSPE and SPE images
TF-M Core responsible for controlling the isolation, communication and execution within SPE and with NSPE
Crypto, Internal Trusted Storage (ITS), Protected Storage (PS) and Attestation secure services
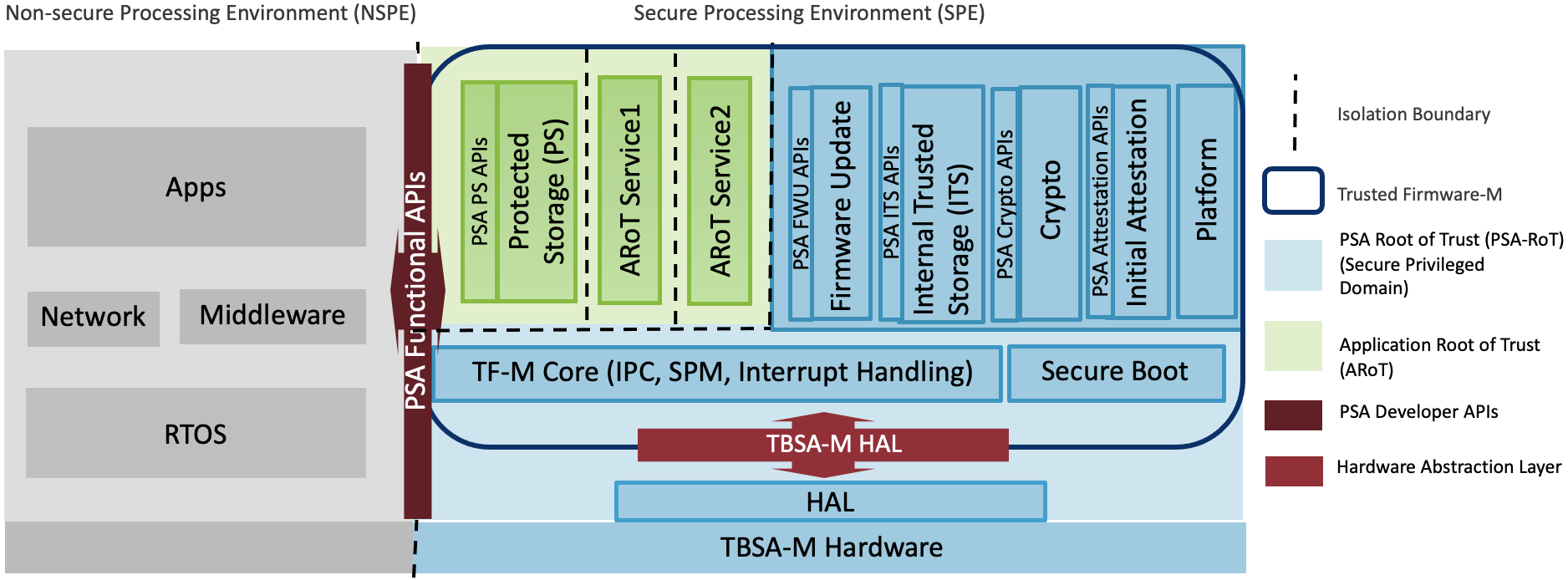
FF-M compliant design with TF-M¶
Applications and Libraries in the Non-secure Processing Environment can utilize these secure services with a standardized set of PSA Functional APIs. Applications running on Cortex-M devices can leverage TF-M services to ensure secure connection with edge gateways and IoT cloud services. It also protects the critical security assets such as sensitive data, keys and certificates on the platform. TF-M is supported on several Cortex-M based Microcontrollers and Real Time Operating Systems (RTOS).
Terms TFM and TF-M are commonly used in documents and code and both
refer to Trusted Firmware M. Glossary has the list
of terms and abbreviations.
2. License¶
The software is provided under a BSD-3-Clause License. Contributions to this project are accepted under the same license with developer sign-off as described in the Contributing Guidelines.
This project contains code from other projects as listed below. The code from
external projects is limited to app, bl2, lib and platform
folders. The original license text is included in those source files.
The
appfolder contains files imported from CMSIS_5 project and the files have Apache 2.0 license.The
bl2folder contains files imported from MCUBoot project and the files have Apache 2.0 license.The
libfolder may contain 3rd party files with diverse licenses.The
platformfolder currently contains platforms support imported from the external project and the files may have different licenses.
3. Getting Started¶
3.1. Prerequisite¶
Trusted Firmware M provides a reference implementation of platform security architecture reference implementation aligning with PSA Certified guidelines. It is assumed that the reader is familiar with specifications can be found at Platform Security Architecture Resources.
The current TF-M implementation specifically targets TrustZone for ARMv8-M so a good understanding of the v8-M architecture is also necessary. A good place to get started with ARMv8-M is developer.arm.com.
3.2. Build and run instructions¶
Trusted Firmware M source code is available on git.trustedfirmware.org.
To build & run TF-M:
Follow the SW requirements guide to set up your environment.
Follow the Build instructions to compile and build the TF-M source.
Follow the User guide for information on running the example.
To port TF-M to a another system or OS, follow the OS Integration Guide
Contributing Guidelines contains guidance on how to contribute to this project.
4. Platforms supported¶
The document Supported Platforms lists the details.
5. Release Notes and Process¶
The Release Cadence and Process provides release cadence and process information.
The Releases provides details of major features of the release and platforms supported.
6. Feedback and support¶
For this release, feedback is requested via email to tf-m@lists.trustedfirmware.org.
Copyright (c) 2017-2021, Arm Limited. All rights reserved.