Actinius Icarus SoM
Overview

Fig. 73 Icarus SoM (nRF9160)
The Icarus SoM is a coin-sized, easy-to-solder cellular IoT Module built around Nordic Semi’s nRF9160 modem and combines LTE-M, NB-IoT, GPS, accelerometer as well as an eSIM and option for an external nano SIM connector.
The main uController is the Nordic Semiconductor nRF9160, with ARM Cortex-M33F CPU, ARMv8-M Security Extension and the following devices (provided directly by Nordic):
ADC
CLOCK
FLASH
GPIO
I2C
MPU
NVIC
PWM
RTC
Segger RTT (RTT Console)
SPI
UARTE
WDT
IDAU
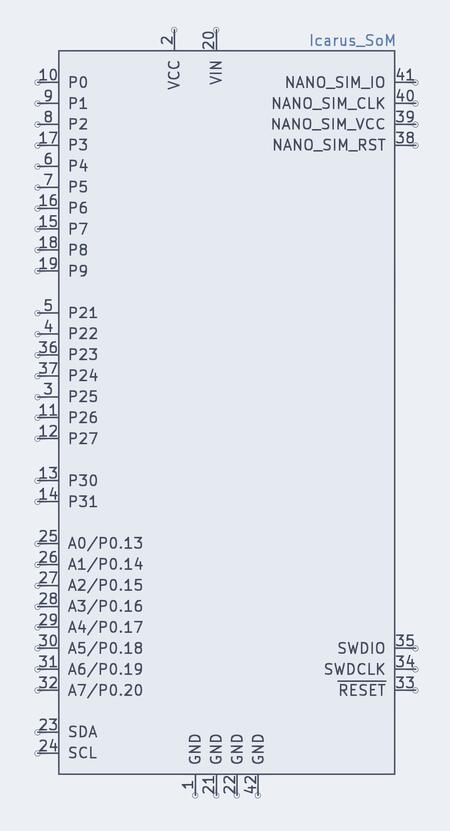
Fig. 74 Icarus SoM Pins

Fig. 75 Internal Pinouts
Hardware
The detailed information about the on-board hardware can be found at the Icarus SoM Product Website 2.
Supported Features
The actinius_icarus_som board configuration supports the following hardware features:
Interface |
Controller |
Driver/Component |
|---|---|---|
ADC |
on-chip |
adc |
CLOCK |
on-chip |
clock_control |
FLASH |
on-chip |
flash |
GPIO |
on-chip |
gpio |
I2C(M) |
on-chip |
i2c |
MPU |
on-chip |
arch/arm |
NVIC |
on-chip |
arch/arm |
PWM |
on-chip |
pwm |
SPI(M/S) |
on-chip |
spi |
SPU |
on-chip |
system protection |
UARTE |
on-chip |
serial |
ACCEL |
st |
lis2dh |
SIM selection
The sim choice (eSIM or nano-SIM) can be configured in Devicetree by adjusting
the sim property in the sim_select node.
Security components
Building Secure/Non-Secure Zephyr applications
The process requires the following steps:
Build the Secure Zephyr application using
-DBOARD=actinius_icarus_som.Build the Non-Secure Zephyr application using
-DBOARD=actinius_icarus_som_ns.Merge the two binaries together.
If you are using Segger Embedded Studio v4.18 or later, the two binaries are built, merged, and burned automatically, unless you have disabled the feature.
When building a Secure/Non-Secure application, the Secure application will have to set the IDAU (SPU) configuration to allow Non-Secure access to all CPU resources utilized by the Non-Secure application firmware. SPU configuration shall take place before jumping to the Non-Secure application.
More information can be found in the Icarus SoM Product Website 2 or the Actinius Documentation Portal 3.
