Bluetooth: Central HIDS
The Central HIDS sample demonstrates how to use the GATT Human Interface Device Service (HIDS) Client to interact with a HIDS server. Basically, the sample simulates a computer that connects to a mouse or a keyboard.
Note
Apart from HID samples, the nRF Connect SDK provides a complete reference application design of Human Interface Device (HID). Depending on the configuration, the application can work as a desktop mouse, gaming mouse, keyboard, or connection dongle. It supports connection over Bluetooth® LE, USB, or both. For details, see the nRF Desktop documentation.
Requirements
The sample supports the following development kits:
Hardware platforms |
PCA |
Board name |
Board target |
|---|---|---|---|
PCA10156 |
|
||
nRF54L15 DK |
PCA10156 |
|
|
PCA10175 |
|
||
PCA10095 |
|
||
PCA10040 |
|
||
PCA10056 |
|
When built for a board target with the */ns variant, the sample is configured to compile and run as a non-secure application with Cortex-M Security Extensions enabled.
Therefore, it automatically includes Trusted Firmware-M that prepares the required peripherals and secure services to be available for the application.
The sample also requires a HIDS device to connect with (for example, another development kit running the Bluetooth: Peripheral HIDS mouse sample or Bluetooth: Peripheral HIDS keyboard sample, or a computer with a Bluetooth Low Energy dongle and nRF Connect for Desktop).
Overview
The sample scans available devices, searching for a HIDS server. If a HIDS server is found, the sample connects to it and discovers all characteristics.
If any input reports are detected, the sample subscribes to them to receive notifications. If any boot reports are detected, the behavior depends on if they are boot mouse reports or boot keyboard reports:
If a boot mouse report is detected, the sample subscribes to it.
If a boot keyboard report is detected, the sample subscribes to its input report, and the sample functionality of changing the CAPSLOCK LED is enabled (Button 1 and Button 3).
If a boot mouse report is detected, the sample subscribes to it.
If a boot keyboard report is detected, the sample subscribes to its input report, and the sample functionality of changing the CAPSLOCK LED is enabled (Button 0 and Button 2).
User interface
- Button 1:
Toggle the CAPSLOCK LED on the connected keyboard using Write without response. This function is available only if the connected keyboard is set to work in Boot Protocol Mode.
When pairing, press this button to confirm the passkey value that is printed on the COM listener to pair with the other device.
- Button 2:
Switch between Boot Protocol Mode and Report Protocol Mode. This function is available only if the connected peer supports the Protocol Mode Characteristic.
When pairing, press this button to reject the passkey value that is printed on the COM listener to prevent pairing with the other device.
- Button 3:
Toggle the CAPSLOCK LED on the connected keyboard using Write with response. This function is available only if the connected HID has boot keyboard reports. It always writes CAPSLOCK information to the boot report, even if Report Protocol Mode is selected.
- Button 0:
Toggle the CAPSLOCK LED on the connected keyboard using Write without response. This function is available only if the connected keyboard is set to work in Boot Protocol Mode.
When pairing, press this button to confirm the passkey value that is printed on the COM listener to pair with the other device.
- Button 1:
Switch between Boot Protocol Mode and Report Protocol Mode. This function is available only if the connected peer supports the Protocol Mode Characteristic.
When pairing, press this button to reject the passkey value that is printed on the COM listener to prevent pairing with the other device.
- Button 2:
Toggle the CAPSLOCK LED on the connected keyboard using Write with response. This function is available only if the connected HID has boot keyboard reports. It always writes CAPSLOCK information to the boot report, even if Report Protocol Mode is selected.
Building and Running
This sample can be found under samples/bluetooth/central_hids in the nRF Connect SDK folder structure.
When built as firmware image for a board target with the */ns variant, the sample has Cortex-M Security Extensions (CMSE) enabled and separates the firmware between Non-Secure Processing Environment (NSPE) and Secure Processing Environment (SPE).
Because of this, it automatically includes the Trusted Firmware-M (TF-M).
To read more about CMSE, see Processing environments.
To build the sample, follow the instructions in Building an application for your preferred building environment. See also Programming an application for programming steps and Testing and optimization for general information about testing and debugging in the nRF Connect SDK.
Note
When building repository applications in the SDK repositories, building with sysbuild is enabled by default.
If you work with out-of-tree freestanding applications, you need to manually pass the --sysbuild parameter to every build command or configure west to always use it.
Note
Programming the nRF54H20 SoC can sometimes fail due to conflicts in the resource configuration. This can happen if, for example, an application programmed to the nRF54H20 SoC configured the UICRs for one or more cores in a way that is incompatible with the configuration required by the application you are trying to program on the SoC.
To fix this error and erase the UICR for the application core, run the following command:
nrfutil device recover --core Application
If your sample also uses the radio core, you must also erase the UICRs for the radio core. To erase the UICR for the radio core, run the following command:
nrfutil device recover --core Network
For more information on the command, run:
nrfutil device recover --help
You can then run west flash to program your application.
Testing
After programming the sample to your development kit, you can test it either by connecting to another development kit that is running the Bluetooth: Peripheral HIDS keyboard sample, or by using nRF Connect for Desktop that emulates a HIDS server.
Testing with another development kit
Connect to the kit that runs this sample with a terminal emulator (for example, nRF Connect Serial Terminal). See Testing and optimization for the required settings and steps.
Reset the kit.
Program the other kit with the Bluetooth: Peripheral HIDS keyboard sample and reset it.
When connected, press Button 1 on both devices to confirm the passkey value used for bonding, or press Button 2 to reject it.
Wait until the HIDS keyboard is detected by the central. All detected descriptors are listed. In the terminal window, check for information similar to the following:
HIDS is ready to work Subscribe to report id: 1 Subscribe to boot keyboard report
Press Button 1 and Button 2 one after another on the kit that runs the keyboard sample and observe the notification values in the terminal window. See Bluetooth: Peripheral HIDS keyboard for the expected values:
Notification, id: 0, size: 8, data: 0x0 0x0 0xb 0x0 0x0 0x0 0x0 0x0 Notification, id: 0, size: 8, data: 0x0 0x0 0x0 0x0 0x0 0x0 0x0 0x0
Press Button 2 on the kit that runs the Central HIDS sample and observe that the protocol mode is updated into boot mode:
Setting protocol mode: BOOT
Press Button 1 and Button 2 one after another on the kit that runs the keyboard sample and observe the notification of the boot report values:
Notification, keyboard boot, size: 8, data: 0x0 0x0 0xf 0x0 0x0 0x0 0x0 0x0 Notification, keyboard boot, size: 8, data: 0x0 0x0 0x0 0x0 0x0 0x0 0x0 0x0
Press Button 1 and Button 3 one after another on the Central HIDS kit and observe that LED 1 on the keyboard kit changes its state. The following information is also displayed in the terminal window.
If Button 1 was pressed:
Caps lock send (val: 0x2) Caps lock sent
If Button 3 was pressed:
Caps lock send using write with response (val: 0x2) Capslock write result: 0 Received data (size: 1, data[0]: 0x2)
Connect to the kit that runs this sample with a terminal emulator (for example, nRF Connect Serial Terminal). See Testing and optimization for the required settings and steps.
Reset the kit.
Program the other kit with the Bluetooth: Peripheral HIDS keyboard sample and reset it.
When connected, press Button 0 on both devices to confirm the passkey value used for bonding, or press Button 1 to reject it.
Wait until the HIDS keyboard is detected by the central. All detected descriptors are listed. In the terminal window, check for information similar to the following:
HIDS is ready to work Subscribe to report id: 1 Subscribe to boot keyboard report
Press Button 0 and Button 1 one after another on the kit that runs the keyboard sample and observe the notification values in the terminal window. See Bluetooth: Peripheral HIDS keyboard for the expected values:
Notification, id: 0, size: 8, data: 0x0 0x0 0xb 0x0 0x0 0x0 0x0 0x0 Notification, id: 0, size: 8, data: 0x0 0x0 0x0 0x0 0x0 0x0 0x0 0x0
Press Button 1 on the kit that runs the Central HIDS sample and observe that the protocol mode is updated into boot mode:
Setting protocol mode: BOOT
Press Button 0 and Button 1 one after another on the kit that runs the keyboard sample and observe the notification of the boot report values:
Notification, keyboard boot, size: 8, data: 0x0 0x0 0xf 0x0 0x0 0x0 0x0 0x0 Notification, keyboard boot, size: 8, data: 0x0 0x0 0x0 0x0 0x0 0x0 0x0 0x0
Press Button 0 and Button 2 one after another on the Central HIDS kit and observe that LED 0 on the keyboard kit changes its state. The following information is also displayed in the terminal window.
If Button 0 was pressed:
Caps lock send (val: 0x2) Caps lock sent
If Button 2 was pressed:
Caps lock send using write with response (val: 0x2) Capslock write result: 0 Received data (size: 1, data[0]: 0x2)
Testing with nRF Connect for Desktop
Connect to the kit that runs this sample with a terminal emulator (for example, nRF Connect Serial Terminal). See Testing and optimization for the required settings and steps.
Reset the kit.
Start nRF Connect for Desktop.
Open the Bluetooth Low Energy app and select the connected dongle that is used for communication.
Open the SERVER SETUP tab. Click the dongle configuration and select Load setup. Load the
hids_keyboard.ncsfile that is located undersamples/bluetooth/central_hidsin the nRF Connect SDK folder structure.Click Apply to device.
Open the CONNECTION MAP tab. Click the dongle configuration and select Advertising setup.
The current version of nRF Connect cannot store the advertising setup, so it must be configured manually. See the following image for the required target configuration:
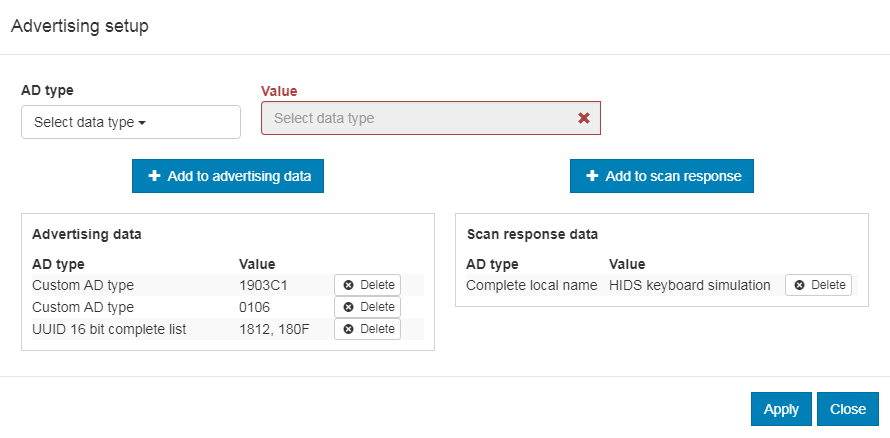
Advertising setup for HIDS keyboard simulator
Complete the following steps to configure the advertising setup:
Delete the default Complete local name from Advertising data.
Add a Custom AD type with AD type value set to
19and Value set to03c1. This is the GAP Appearance advertising data.Add a Custom AD type with AD type value set to
01and Value set to06. This is the AD data with “General Discoverable” and “BR/EDR not supported” flags set.Add a UUID 16 bit complete list with two comma-separated values:
1812and180F. These are the values for HIDS and BAS.Add a Complete local name of your choice to the Scan response data.
Click Apply and Close.
In the Adapter settings, select Start advertising.
Wait until the kit that runs the Central HIDS sample connects. All detected descriptors are listed. Check for information similar to the following:
HIDS is ready to work Subscribe in report id: 1 Subscribe in boot keyboard report
Explore the first report inside Human Interface Device (the one with eight values). Change any of the values and note that the kit logs the change.
Press Button 2 on the kit and observe that the Protocol Mode value changes from
01to00.Press Button 1 and Button 3 one after another and observe that the Boot Keyboard Output Report value toggles between
00and02.
Connect to the kit that runs this sample with a terminal emulator (for example, nRF Connect Serial Terminal). See Testing and optimization for the required settings and steps.
Reset the kit.
Start nRF Connect for Desktop.
Open the Bluetooth Low Energy app and select the connected dongle that is used for communication.
Open the SERVER SETUP tab. Click the dongle configuration and select Load setup. Load the
hids_keyboard.ncsfile that is located undersamples/bluetooth/central_hidsin the nRF Connect SDK folder structure.Click Apply to device.
Open the CONNECTION MAP tab. Click the dongle configuration and select Advertising setup.
The current version of nRF Connect cannot store the advertising setup, so it must be configured manually. See the following image for the required target configuration:

Advertising setup for HIDS keyboard simulator
Complete the following steps to configure the advertising setup:
Delete the default Complete local name from Advertising data.
Add a Custom AD type with AD type value set to
19and Value set to03c1. This is the GAP Appearance advertising data.Add a Custom AD type with AD type value set to
01and Value set to06. This is the AD data with “General Discoverable” and “BR/EDR not supported” flags set.Add a UUID 16 bit complete list with two comma-separated values:
1812and180F. These are the values for HIDS and BAS.Add a Complete local name of your choice to the Scan response data.
Click Apply and Close.
In the Adapter settings, select Start advertising.
Wait until the kit that runs the Central HIDS sample connects. All detected descriptors are listed. Check for information similar to the following:
HIDS is ready to work Subscribe in report id: 1 Subscribe in boot keyboard report
Explore the first report inside Human Interface Device (the one with eight values). Change any of the values and note that the kit logs the change.
Press Button 1 on the kit and observe that the Protocol Mode value changes from
01to00.Press Button 0 and Button 2 one after another and observe that the Boot Keyboard Output Report value toggles between
00and02.
Dependencies
This sample uses the following nRF Connect SDK libraries:
In addition, it uses the following Zephyr libraries:
include/sys/byteorder.hinclude/zephyr/types.hlib/libc/minimal/include/errno.hinclude/sys/printk.hAPI:
include/bluetooth/bluetooth.hinclude/bluetooth/gatt.hinclude/bluetooth/hci.hinclude/bluetooth/conn.hinclude/bluetooth/uuid.h
The sample also uses the following secure firmware component:
