Getting started with nRF7002 DK
The nRF7002 DK (PCA10143) is a single-board development kit for evaluation and development on the Nordic nRF7002, a Wi-Fi companion IC to Nordic nRF5340 System-on-Chip (SoC) host processor.
Overview
The nRF7002 is an IEEE 802.11ax (Wi-Fi 6) compliant solution that implements the Wi-Fi physical layer and MAC layer protocols. It implements the Wi-Fi driver software on the nRF5340 host processor communicating over the QSPI bus.
The nRF5340 host is a dual-core SoC based on the Arm® Cortex®-M33 architecture. It has the following features:
A full-featured Arm Cortex-M33F core with DSP instructions, FPU, and Armv8-M Security Extension, running at up to 128 MHz, referred to as the application core.
A secondary Arm Cortex-M33 core, with a reduced feature set, running at a fixed 64 MHz, referred to as the network core.
The nrf7002dk_nrf5340_cpuapp build target provides support for the application core on the nRF5340 SoC.
The nrf7002dk_nrf5340_cpunet build target provides support for the network core on the nRF5340 SoC.
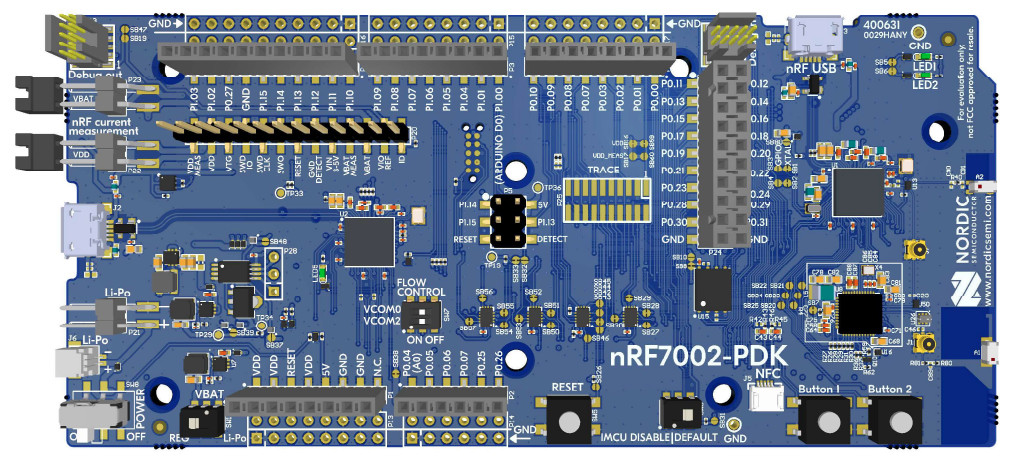
nRF7002 PDK (Preview DK will later be replaced by the certified nRF7002 DK)
Hardware
The nRF7002 DK has two external oscillators:
The frequency of the slow clock is 32.768 kHz.
The frequency of the main clock is 32 MHz.
Supported features
The nrf7002dk_nrf5340_cpuapp board configuration supports the following hardware features:
Interface |
Controller |
Driver/Component |
|---|---|---|
ADC |
on-chip |
adc |
CLOCK |
on-chip |
clock_control |
FLASH |
on-chip |
flash |
GPIO |
on-chip |
gpio |
I2C(M) |
on-chip |
i2c |
MPU |
on-chip |
arch/arm |
NVIC |
on-chip |
arch/arm |
PWM |
on-chip |
pwm |
RTC |
on-chip |
system clock |
RTT |
Segger |
console |
RADIO |
nrf7002 |
Wi-Fi 6 (802.11ax) |
QSPI |
on-chip |
qspi |
SPI(M/S) |
on-chip |
spi |
SPU |
on-chip |
system protection |
UARTE |
on-chip |
serial |
USB |
on-chip |
usb |
WDT |
on-chip |
watchdog |
The nrf7002dk_nrf5340_cpunet board configuration supports the following hardware features:
Interface |
Controller |
Driver/Component |
|---|---|---|
CLOCK |
on-chip |
clock_control |
FLASH |
on-chip |
flash |
GPIO |
on-chip |
gpio |
I2C(M) |
on-chip |
i2c |
MPU |
on-chip |
arch/arm |
NVIC |
on-chip |
arch/arm |
RADIO |
on-chip |
Bluetooth, ieee802154 |
RTC |
on-chip |
system clock |
RTT |
Segger |
console |
QSPI |
on-chip |
qspi |
SPI(M/S) |
on-chip |
spi |
UARTE |
on-chip |
serial |
WDT |
on-chip |
watchdog |
Other hardware features are not supported by the nRF Connect SDK kernel.
Connections and IOs
The connections and IOs supported by the development kit are listed in this section.
LED
LED1 (green) = P1.06
LED2 (green) = P1.07
Wi-Fi control
BUCKEN = P0.12
IOVDD CONTROL = P0.31
HOST IRQ = P0.23
COEX_REQ = P0.28
COEX_STATUS0 = P0.30
COEX_STATUS1 = P0.29
COEX_GRANT = P0.24
Security components
The following security components are available:
Implementation Defined Attribution Unit (IDAU) on the application core.
The IDAU is implemented with the System Protection Unit and is used to define secure and non-secure memory maps. By default, the entire memory space (Flash, SRAM, and peripheral address space) is defined to be secure-accessible only.
Secure boot.
Programming and debugging
The nRF5340 application core supports the Armv8-M Security Extension.
Applications built for the nrf7002dk_nrf5340_cpuapp board boot by default in the secure state.
The nRF5340 network core does not support the Armv8-M Security Extension. nRF5340 IDAU can configure bus accesses by the nRF5340 network core to have the secure attribute set. This allows to build and run secure-only applications on the nRF5340 SoC.
Building secure/non-secure nRF Connect SDK applications with Arm TrustZone
Applications on the nRF5340 can contain both a secure and a non-secure firmware image for the application core. You can build the secure image using either nRF Connect SDK or Trusted Firmware M (TF-M). You must always build the non-secure firmware images using nRF Connect SDK.
Note
By default, the secure image for the nRF5340 application core is built using TF-M.
Building the firmware with TF-M
To build the secure firmware image using TF-M and the non-secure firmware image using nRF Connect SDK, complete the following steps:
Build the non-secure nRF Connect SDK application for the application core using the
nrf7002dk_nrf5340_cpuapp_nsbuild target.To invoke the building of TF-M, the nRF Connect SDK build system requires the Kconfig option
CONFIG_BUILD_WITH_TFMto be enabled, which is set by default when building nRF Connect SDK as a non-secure application.The nRF Connect SDK build system performs the following steps automatically:
Build the non-secure firmware image as a regular nRF Connect SDK application.
Build a TF-M (secure) firmware image.
Merge the output image binaries.
Optionally, build a bootloader image (MCUboot).
Note
Depending on the TF-M configuration, an application DTS overlay can be required to adjust the non-secure image flash memory partition and SRAM starting address and sizes.
Build the application firmware for the network core using the
nrf7002dk_nrf5340_cpunetbuild target.
Building the secure firmware using nRF Connect SDK
To build the secure and the non-secure firmware images using nRF Connect SDK, complete the following steps:
Build the secure nRF Connect SDK application for the application core using the
nrf7002dk_nrf5340_cpuappbuild target.Also set
CONFIG_TRUSTED_EXECUTION_SECUREtoyandCONFIG_BUILD_WITH_TFMtonin the application project configuration file.Build the non-secure nRF Connect SDK application for the application core using the
nrf7002dk_nrf5340_cpuapp_nsbuild target.Merge the two binaries.
Build the application firmware for the network core using the
nrf7002dk_nrf5340_cpunetbuild target.
When building a secure and non-secure application for the nRF5340 application core, the secure application must set the IDAU (SPU) configuration to allow non-secure access to all CPU resources used by the non-secure application firmware. SPU configuration must be applied before jumping to the non-secure application.
Building a secure-only application
Build the nRF Connect SDK application as described in Building and programming an application, using the nrf7002dk_nrf5340_cpuapp build target for the firmware running on the nRF5340 application core and the nrf7002dk_nrf5340_cpunet build target for the firmware running on the nRF5340 network core.
Programming the firmware to the DK
Follow the instructions in the Building and programming an application page to build and flash applications.
Note
To flash and debug applications on the nRF7002 DK you must use the nRF Command Line Tools version 10.12.0 or above. For further information on how to install the nRF Command Line Tools, see Updating repositories and tools.
Debugging
See the Testing and debugging an application page for information about debugging.
