|
nRF5 IoT SDK
v0.9.0
|
|
nRF5 IoT SDK
v0.9.0
|
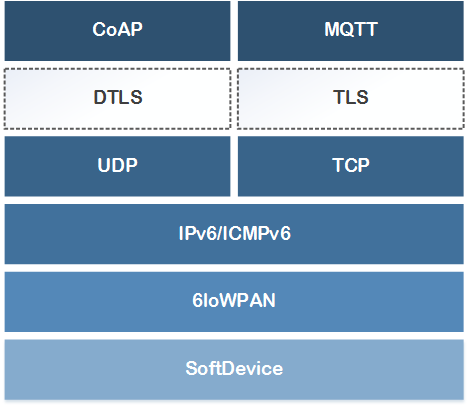
Transport Layer Security (TLS) ensures privacy between server and client endpoints by providing protection against eavesdropping and the tampering of data exchanged between the communicating endpoints.
The Datagram Transport Layer Security (DTLS) defines transport layer security for datagram protocols thereby providing communications privacy for datagram protocols. The DTLS protocol is based on the Transport Layer Security (TLS) protocol and provides equivalent security guarantees. TLS assumes a reliable transport and breaks when re-hosted on an unreliable transport. DTLS aims at fixing this problem by proposing changes to allow the reordering of packets and by implementing retransmission timers to handle packet loss.
CoAP defines DTLS bindings for secure communication. MQTT defines bindings for TLS.
Figure 2 below shows the position of the TLS/DTLS layers in the Nordic IoT SDK.
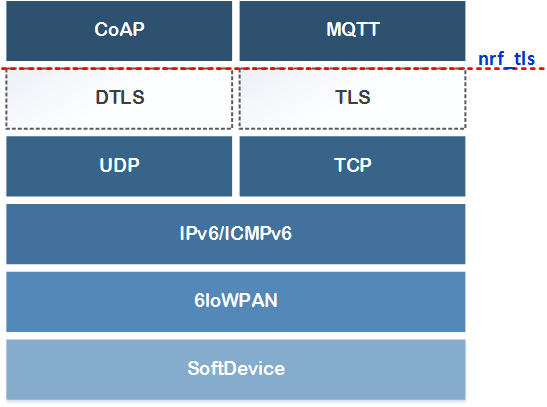
To avoid binding the users of the SDK with a specific TLS library, an abstracted interface is used in the SDK. This abstraction of TLS/DTLS is defined in TLS on nRF5x. CoAP and MQTT rely on availability of this interface for securing their respective transport layers.
In the SDK, mbedtls is used to provide the TLS interface to the IoT protocols.
Currently DTLS and TLS are maintained as two different configurations. The table below summarizes the features supported in the two configurations.
| Feature | DTLS | TLS |
|---|---|---|
| Role | Server and Client | Client only |
| Ciphers | TLS_PSK_WITH_AES_128_CCM_8 | TLS_PSK_WITH_AES_128_CBC_SHA TLS_PSK_WITH_AES_256_CBC_SHA TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA |
| Max Fragment Length | 1024 | 3072 |
| Maximum concurrent sessions | 2 | 1 |
Configuration of mbedtls as TLS client used in all MQTT examples can be found at
<InstallFolder>components/iot/tls/mbedtls/tls/config. Configuration of mbedtls as DTLS server and client used for CoAP DTLS examples can be found at
<InstallFolder>components/iot/tls/mbedtls/dtls/config.
This section describes the application interface of this module.
The repository for mbedtls source is located at mbedTLS GitHub. mbedtls version included in the SDK is the tag mbedtls-2.2.0, corresponding hash is 8254ed2a9fadede8c6bf414072f78fc78d5af61c.